





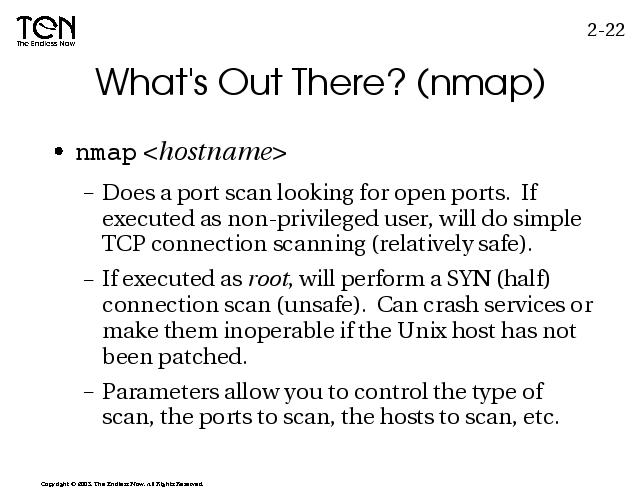
Notes:
The nmap program supports many options. With it you can effectively scan a network for open ports and do OS finger printing. But nmap can be perceived as an attack on a network. In some cases, a well configured firewall will temporarily disable packets from the “attacking” host. There some experimental options which allow you to do a “zombie” scan which will make the host believe the packets are coming from somwhere else. Obviously, this could definitely be construed as an aggressive attack (WARNING).
To scan a host that does not reply to pings:
# nmap -P0 <hostname>
To scan for hosts for ones which have either smtp or ssh ports open on the 192.168.1 network.
$ nmap -p 22,25 192.168.1.*
To scan for the SNMP port (UDP) on the 192.168.1 network:
# nmap -sU -p 161 192.168.1.*
(Note: RFC 1812 documents a limiting of ICMP error rate which most Unix/Linux hosts have implemented. This will greatly slow down the rate at which you can do UDP scanning. Many non-Unix OS's do not implement the suggestions of RFC 1812 though which makes scanning those hosts extremely quick.)
To do a finger print scan on a host:
# nmap -O localhost
tarting nmap V. 3.00 ( www.insecure.org/nmap/ )
Interesting ports on localhost (127.0.0.1):
(The 1596 ports scanned but not shown below are in state: closed)
Port State Service
22/tcp open ssh
25/tcp open smtp
111/tcp open sunrpc
631/tcp open ipp
6000/tcp open X11
Remote operating system guess: Linux Kernel 2.4.0 - 2.5.20
Uptime 0.123 days (since Thu Mar 20 08:52:45 2003)
Nmap run completed -- 1 IP address (1 host up) scanned in 7 seconds












