|
1825 Monetary Lane Suite #104 Carrollton, TX
Do a presentation at NTLUG.
What is the Linux Installation Project?
Real companies using Linux!
Not just for business anymore.
Providing ready to run platforms on Linux
|
Show Descriptions... (Show All/All+Images)
(Single Column)

- Kernel prepatch 6.16-rc5
The 6.16-rc5 kernel prepatch has beenreleased. Quoth Linus: "Please keep testing, but this all feels fairlyregular for this phase of the release".
- [$] Python audio processing with pedalboard
ThePyCon US 2025, which was held in Pittsburgh,Pennsylvania in May. He started from the basics of digital audio and thenmoved into working with pedalboard. There were, as might be guessed, audio examplesin the talk, along with some visual information; interested readers may want to view the YouTube video of thepresentation.
- Security updates for Friday
Security updates have been issued by AlmaLinux (.NET 9.0, container-tools:rhel8, ghostscript, git-lfs, grafana-pcp, pandoc, perl-FCGI:0.78, ruby:2.5, ruby:3.3, tigervnc, and varnish:6), Debian (jpeg-xl and mediawiki), Fedora (darktable, guacamole-server, mingw-gdk-pixbuf, and yarnpkg), Oracle (gimp, kernel, libsoup, python-tornado, python3.12, and thunderbird), Slackware (php), SUSE (libgepub), and Ubuntu (libtpms, linux-aws-5.15, linux-intel-iot-realtime, and linux-bluefield).
- Richards: Introducing tmux-rs
Collin Richards has announced version0.0.1 of tmux-rs, a port of the tmux terminal multiplexerto Rust.
For the [past] 6 months or so I've been quietly porting tmux from C toRust. I've recently reached a big milestone: the code base is now 100%(unsafe) Rust. I'd like to share the process of porting the originalcodebase from ~67,000 lines of C code to ~81,000 lines of Rust(excluding comments and empty lines). You might be asking: why did yourewrite tmux in Rust? And yeah, I don't really have a goodreason. It's a hobby project. Like gardening, but with more segfaults.
Richards says that the next goal for the project is to convert itto safe Rust. It is currently "not very difficult to get it tocrash", but he wanted to share the project with other Rust fansnow. The project is available onGitHub.
- [$] Kernel API specification and validation
The kernel project makes a strong promise to its users: the kernel ABI willnot be changed in ways that break user-space code. The occasional failurenotwithstanding, kernel developers do try to live up to that promise. Theyare handicapped by one little problem, though: there is no description ofwhat the kernel ABI is, and no comprehensive way to test whether a givenchange breaks it. The kernel APIspecification framework proposed (in its second revision) by SashaLevin addresses some of those concerns, but the solution is incomplete anddoes not come for free.
- Security updates for Thursday
Security updates have been issued by AlmaLinux (.NET 9.0, aardvark-dns, apache-commons-beanutils, bootc, buildah, corosync, delve and golang, exiv2, expat, firefox, ghostscript, git, git-lfs, gnutls, grafana, grafana-pcp, grub2, gstreamer1, gstreamer1-plugins-bad-free, gstreamer1-plugins-ugly-free, and gstreamer1-rtsp-server, gstreamer1-plugins-base, gstreamer1-plugins-good, gvisor-tap-vsock, iptraf-ng, java-21-openjdk, kernel, keylime-agent-rust, krb5, libarchive, libblockdev, libsoup3, libtasn1, libvpx, libxslt, microcode_ctl, mod_auth_openidc, nodejs22, nodejs:20, openjpeg2, osbuild and osbuild-composer, perl-FCGI, perl-Module-ScanDeps, perl-YAML-LibYAML, php, php:8.2, php:8.3, podman, protobuf, python-jinja2, python-requests, python3.11, python3.12, python3.12-cryptography, python3.9, rpm-ostree, rsync, rust-bootupd, skopeo, thunderbird, tigervnc, tomcat, tomcat9, webkit2gtk3, xdg-utils, xorg-x11-server, and xorg-x11-server-Xwayland), Debian (ring), Mageia (libarchive and rootcerts, nss & firefox), Oracle (.NET 9.0, corosync, firefox, osbuild-composer, pam, python3, python3.11, python3.12, python3.9, skopeo, sudo, and thunderbird), Red Hat (microcode_ctl, pam, php, thunderbird, tigervnc, xorg-x11-server, xorg-x11-server and xorg-x11-server-Xwayland, and xorg-x11-server-Xwayland), SUSE (clamav, icu, libgepub, libsoup, python-requests, tomcat, and xorg-x11-server), and Ubuntu (clamav, logback, mongo-c-driver, pcs, and python-flask-cors).
- [$] LWN.net Weekly Edition for July 3, 2025
Inside this week's LWN.net Weekly Edition:
Front: Kernel features from Python; i686 in Fedora; Kernel development with LLMs; Rust drivers; Load balancing with machine learning; Transparent huge pages. Briefs: Bcachefs removal; Coccinelle for Rust; Netdev Foundation; Oracle Linux 10; GNU HHIS 5.0; Rust 1.88.0; Quotes; ... Announcements: Newsletters, conferences, security updates, patches, and more.
- Debian looking for testers with Apple M1/M2 machines
Debian's Bananas team has putout a call for people with Apple M1 or M2 systems to help testDebian on those machines:
The Bananas Team has set up an installer at with images for GNOME, KDE and console installations. While we'd like to build an actual Debian installer sooner or later (we may need a heads-up from the Debian Images team for that), at this time we only provide an asahi-type installer, which installs both the "bootloader" and the OS partitions to disk from the network (as opposed to only installing the bootloader and then letting you install Debian using a d-i USB stick). We haven't forked Trixie from Testing yet, so what you'll get is Debian Testing quite deep into the freeze.
- The Netdev Foundation launches
The NetdevFoundation, which is "a user-led effort under the supervision of theLinux Foundation, focused on financially supporting Linux networkingdevelopment", has announced itsexistence.
The initial motivation was to move the NIPA testing outside of Meta, so that more people can help and contribute. But there should be sufficient budget to sponsor more projects.
(NIPA is NetdevInfrastructure for Patch Automation).
- Linux 6.16 Performance Regression Tracked Down In New Futex Code
Sent out this morning as part of this week's "locking/urgent" pull request is a performance regression fix ahead of today's Linux 6.16-rc5 release. This latest performance regression in the Linux kernel is around the new Futex code merged this cycle with a big performance hit being observed in scheduler benchmarks...
- 9to5Linux Weekly Roundup: July 6th, 2025
The 247th installment of the 9to5Linux Weekly Roundup is here for the week ending on July 6th, 2025, keeping you updated with the most important things happening in the Linux world.

- Citizen Scientists Just Helped Discover Nearly 8,000 New Eclipsing Binary Stars
"Citizen scientists have successfully located thousands of previously unknown pairs of 'eclipsing binary' stars," reports the Washington Post, citing a recent announcement from NASA.The ongoing initiative helps space researchers hunt for "eclipsing binary" stars, a rare phenomenon in which two stars orbit one another, periodically blocking each other's light. These star pairs offer important data to astrophysicists, who consider the many measurable properties of eclipsing binaries — and the information they bear about the history of star formation and destruction — as a foundation of the field... The citizen science project in question, the Eclipsing Binary Patrol, validates images from NASA's Transiting Exoplanet Survey Satellite (TESS) mission. The satellite, launched in 2018, is "exceptionally capable at detecting varying stars," the researchers write in a preprint paper describing the initiative. The researchers used machine learning to identify about 1.2 million potential eclipsing star pairs. Citizen scientists then validated a subset of about 60,000... manually inspecting hundreds of thousands of images of eclipse-like events and weeding out actual binaries from images that tricked the algorithm. "Thankfully," the researchers write, "to the rescue come volunteers from all walks of life that boost the capacity of bandwidth-limited professional astronomers many-fold and help tackle the ever-increasing volume of publicly available astronomical data." Universe Today describes how they limited the dataset to only stars with a magnitude brighter than 15, then used a Python tool to generate a massive dataset of millions of light curves...The outcome of all the work resulted in the identification of 10,001 eclipsing binary systems. 7,936 of them are new to science, while the other 2,065 were previously known, but the study provided updated, more accurate, parameters for their periods, as TESS' dataset provided better insight. There were also some particularly interesting systems that could hold new discoveries, including several that had variable eclipse timings, and plenty that might have a third star, and some that show a significant dynamic between the star being orbited and the one doing the orbiting. All of those systems await further research, but there's another, unspoken factor at play in this data — exoplanets. TESS was originally designed as an exoplanet hunter, and this kind of large scale AI/human collaboration of lightcurve analysis is exactly the kind of work that could potentially produce even more accurate exoplanet catalogues, as evidenced by some of the work already done in this paper. That seems to be the next step for this dataset, with Dr. Kostov telling an interviewer "I can't wait to search them for exoplanets!" Given the data has already been collected, and the team has already been assembled, it's very likely he'll get his chance soon.
 
Read more of this story at Slashdot.
- Google DeepMind's Spinoff Company 'Very Close' to Human Trials for Its AI-Designed Drugs
Google DeepMind's chief business officer says Alphabet's drug-discovery company Isomorphic Labs "is preparing to launch human trials of AI-designed drugs," according to a report in Fortune, "pairing cutting-edge AI with pharma veterans to design medicines faster, cheaper, and more accurately.""There are people sitting in our office in King's Cross, London, working, and collaborating with AI to design drugs for cancer," said Colin Murdoch [DeepMind's chief business officer and president of Isomorphic Labs]. "That's happening right now." After years in development, Murdoch says human clinical trials for Isomorphic's AI-assisted drugs are finally in sight. "The next big milestone is actually going out to clinical trials, starting to put these things into human beings," he said. "We're staffing up now. We're getting very close." The company, which was spun out of DeepMind in 2021, was born from one of DeepMind's most celebrated breakthroughs, AlphaFold, an AI system capable of predicting protein structures with a high level of accuracy. Interactions of AlphaFold progressed from being able to accurately predict individual protein structures to modeling how proteins interact with other molecules like DNA and drugs. These leaps made it far more useful for drug discovery, helping researchers design medicines faster and more precisely, turning the tool into a launchpad for a much larger ambition... In 2024, the same year it released AlphaFold 3, Isomorphic signed major research collaborations with pharma companies Novartis and Eli Lilly. A year later, in April 2025, Isomorphic Labs raised $600 million in its first-ever external funding round, led by Thrive Capital. The deals are part of Isomorphic's plan to build a "world-class drug design engine..." Today, pharma companies often spend millions attempting to bring a single drug to market, sometimes with just a 10% chance of success once trials begin. Murdoch believes Isomorphic's tech could radically improve those odds. "We're trying to do all these things: speed them up, reduce the cost, but also really improve the chance that we can be successful," he says. He wants to harness AlphaFold's technology to get to a point where researchers have 100% conviction that the drugs they are developing are going to work in human trials. "One day we hope to be able to say — well, here's a disease, and then click a button and out pops the design for a drug to address that disease," Murdoch said. "All powered by these amazing AI tools."
 
Read more of this story at Slashdot.
- Chinese Film Foundation Plans to Use AI to 'Revitalize' 100 Classic Kung Fu Films
"The China Film Foundation, a nonprofit fund under the Chinese government, plans to use AI to revitalize 100 kung fu classics including Police Story, Once Upon a Time in China and Fist of Fury, featuring Jackie Chan, Jet Li and Bruce Lee, respectively," reports the Los Angeles Times. "The foundation said it will partner with businesses including Shanghai Canxing Culture & Media Co., which will license 100 Hong Kong films to AI companies to reintroduce those movies to younger audiences globally."The foundation said there are opportunities to use AI to tell those stories through animation, for example. There are plans to release an animated version of director John Woo's 1986 film A Better Tomorrow that uses AI to "reinterpret" Woo's "signature visual language," according to an English transcript of the announcement.... The project raised eyebrows among U.S. artists, many of whom are deeply wary of the use of AI in creative pursuits. The Directors Guild of America said AI is a creative tool that should only be used to enhance the creative storytelling process and "it should never be used retroactively to distort or destroy a filmmaker's artistic work... The DGA strongly opposes the use of AI or any other technology to mutilate a film or to alter a director's vision," the DGA said in a statement. "The Guild has a longstanding history of opposing such alterations on issues like colorization or sanitization of films to eliminate so-called 'objectionable content', or other changes that fundamentally alter a film's original style, meaning, and substance." The project highlights widely divergent views on AI's potential to reshape entertainment as the two countries compete for dominance in the highly competitive AI space.... During the project's announcement, supporters touted the opportunity AI will bring to China to further its cultural message globally and generate new work for creatives. At the same time, they touted AI's disruption of the filmmaking process, saying the A Better Tomorrow remake was completed with just 30 people, significantly fewer than a typical animated project. China is a "more brutal society in that sense," said Eric Harwit, professor of Asian studies at the University of Hawaii at Manoa. "If somebody loses their job because artificial intelligence is taking over, well, that's just the cost of China's moving forward.... You don't have those freestanding labor organizations, so they don't have that kind of clout to protest against the Chinese using artificial intelligence in a way that might reduce their job opportunities or lead to layoffs in the sector..." The kung fu revitalization efforts will extend into other areas, including the creation of a martial arts video game. The article also includes an interesting statistic. "Many people in China embrace AI, with 83% feeling confident that AI systems are designed to act in the best interest of society, much higher than the U.S. where it's 37%, according to a survey from the United Nations Development Program."
 
Read more of this story at Slashdot.
- Recent College Graduates Face Higher Unemployment Than Other Workers - for the First Time in Decades
"A growing group of young, college-educated Americans are struggling to find work," reports the Minnesota Star Tribune, "as the unemployment rate for recent graduates outpaces overall unemployment for the first time in decades."While the national unemployment rate has hovered around 4% for months, the rate for 20-something degree holders is nearly 6%, data from the Federal Reserve Bank of New York shows. [And for young workers (ages 22 to 27) without a degree it's 6.9%.] The amount of time young workers report being unemployed is also on the rise. Economists attribute some of the shift to normal post-pandemic cooling of labor market, which is making it harder for job-seekers of all ages to land a gig. But there's also widespread economic uncertainty causing employers to pull back on hiring and signs AI could replace entry-level positions.... Business schools nationwide were among the first to see the labor market shift in early 2023 as tech industry cuts bled into other sectors, said Maggie Tomas, Business Career Center executive director at Carlson. Tariffs and stock market volatility have only added to the uncertainty, she said. In 2022, when workers had their pick of jobs, 98% of full-time Carlson MBA graduates had a job offer in a field related to their degree within three months of graduation, according to the school. That number, which Tomas said is usually 90% or higher, dropped to 89% in 2023 and 83% in 2024. Part of the challenge, she said, is recent graduates are now competing with more experienced workers who are re-entering the market amid layoffs and hiring freezes... After doing a lot of hiring in 2021 and 2022, Securian Financial in St. Paul is prioritizing internal hires, said Human Resources Director Leah Henrikson. Many entry-level roles have gone to current employees looking for a change, she said. "We are still looking externally, it's just the folks that we are looking for externally tend ... to fulfill a specific skill gap we may have at that moment in time," Henrikson said.
 
Read more of this story at Slashdot.
- Simulation of Crashed Boeing 787 Put Focus on a Technical Flaw
Investigators of a deadly Boeing 787 crash "are studying possible dual engine failure as a scenario that prevented the Boeing Co. 787 jet from staying airborne," reports Bloomberg:Pilots from the airline reenacted the doomed aircraft's parameters in a flight simulator, including with the landing gear deployed and the wing flaps retracted, and found those settings alone didn't cause a crash, according to people familiar with the investigation. [Also, analysis of the wreckage "suggests the wing flaps and slats, which help an aircraft increase lift during takeoff, were extended correctly."] The result, alongside the previous discovery that an emergency-power turbine deployed seconds before impact, has reinforced the focus on a technical failure as one possible cause, said the people, who asked not to be identified discussing nonpublic deliberations... [The turbine deploys "in the case of electrical failure," the article points out, and "was activated before the plane crashed, according to previous findings. That fan helps provide the aircraft with vital power, though it's far too small to generate any lift."] Pilots who reviewed the footage have pointed to the fact that the landing gear was already partially tilted forward, suggesting the cockpit crew had initiated the retraction sequence of the wheels. At the same time, the landing-gear doors had not opened, which pilots say might mean that the aircraft experienced a loss of power or a hydraulic failure — again pointing to possible issues with the engines that provide the aircraft's electricity.
 
Read more of this story at Slashdot.
- Drones Used by California Cities to Patrol for Illegal Fireworks and Issue Fines
"California residents who lit illegal fireworks over the July 4 holiday may be in for a nasty surprise in the mail thanks to covert fire department operations," reports SFGate. "A number of California cities, including Sacramento, have begun using drones to locate people shooting off illegal fireworks."From Wednesday to Saturday night, the Sacramento Fire Department's special fireworks task force patrolled the streets with unmarked cars and drones, focusing on neighborhoods where they've had prior complaints. Task force officers and the drones took photos of the illegal activity, and within 30 days the property owner where the fireworks were used could receive a fine in the mail... This year, Sacramento upped the fine to $1,000 for the first firework, $2,500 for the second and $5,000 per firework after that. If you lit a firework on city property, such as a park or a school, the fine goes up to $10,000 each. There's no limit to how many fines you can be issued... This year, a number of cities across the state announced they would be using drones to find scofflaws, among them Indio, Riverside, Hemet, Brea and towns in Tulare County... Fox40 reported on Saturday that around 60 citations were being prepared in Sacramento, with more likely on the way as fire officials review surveillance footage. Last year for illegal fireworks, one Sacramento-area resident received a $100,000 fine.
 
Read more of this story at Slashdot.
- Is China Quickly Eroding America's Lead in the Global AI Race?
China "is pouring money into building an AI supply chain with as little reliance on the U.S. as possible," reports the Wall Street Journal. And now Chinese AI companies "are loosening the U.S.'s global stranglehold on AI," reports the Wall Street Journal, "challenging American superiority and setting the stage for a global arms race in the technology."In Europe, the Middle East, Africa and Asia, users ranging from multinational banks to public universities are turning to large language models from Chinese companies such as startup DeepSeek and e-commerce giant Alibaba as alternatives to American offerings such as ChatGPT... Saudi Aramco, the world's largest oil company, recently installed DeepSeek in its main data center. Even major American cloud service providers such as Amazon Web Services, Microsoft and Google offer DeepSeek to customers, despite the White House banning use of the company's app on some government devices over data-security concerns. OpenAI's ChatGPT remains the world's predominant AI consumer chatbot, with 910 million global downloads compared with DeepSeek's 125 million, figures from researcher Sensor Tower show. American AI is widely seen as the industry's gold standard, thanks to advantages in computing semiconductors, cutting-edge research and access to financial capital. But as in many other industries, Chinese companies have started to snatch customers by offering performance that is nearly as good at vastly lower prices. A study of global competitiveness in critical technologies released in early June by researchers at Harvard University found China has advantages in two key building blocks of AI, data and human capital, that are helping it keep pace... Leading Chinese AI companies — which include Tencent and Baidu — further benefit from releasing their AI models open-source, meaning users are free to tweak them for their own purposes. That encourages developers and companies globally to adopt them. Analysts say it could also pressure U.S. rivals such as OpenAI and Anthropic to justify keeping their models private and the premiums they charge for their service... On Latenode, a Cyprus-based platform that helps global businesses build custom AI tools for tasks including creating social-media and marketing content, as many as one in five users globally now opt for DeepSeek's model, according to co-founder Oleg Zankov. "DeepSeek is overall the same quality but 17 times cheaper," Zankov said, which makes it particularly appealing for clients in places such as Chile and Brazil, where money and computing power aren't as plentiful... The less dominant American AI companies are, the less power the U.S. will have to set global standards for how the technology should be used, industry analysts say. That opens the door for Beijing to use Chinese models as a Trojan horse for disseminating information that reflects its preferred view of the world, some warn.... The U.S. also risks losing insight into China's ambitions and AI innovations, according to Ritwik Gupta, AI policy fellow at the University of California, Berkeley. "If they are dependent on the global ecosystem, then we can govern it," said Gupta. "If not, China is going to do what it is going to do, and we won't have visibility."The article also warns of other potential issues:"Further down the line, a breakdown in U.S.-China cooperation on safety and security could cripple the world's capacity to fight future military and societal threats from unrestrained AI.""The fracturing of global AI is already costing Western makers of computer chips and other hardware billions in lost sales... Adoption of Chinese models globally could also mean lost market share and earnings for AI-related U.S. firms such as Google and Meta."
 
Read more of this story at Slashdot.
- The FSF Faces Active 'Ongoing and Increasing' DDoS Attacks
The Free Software Foundation's services face "ongoing (and increasing) distributed denial of service (DDoS) attacks," senior systems administrator Ian Kelling wrote Wednesday. But "Even though we are under active attack, gnu.org, ftp.gnu.org, and savannah.gnu.org are up with normal response times at the moment, and have been for the majority of this week, largely thanks to hard work from the Savannah hackers Bob, Corwin, and Luke who've helped us, your sysadmins." "We've shielded these sites for almost a full year of intense attacks now, and we'll keep on fighting these attacks for as long as they continue."Our infrastructure has been under attack since August 2024. Large Language Model (LLM) web crawlers have been a significant source of the attacks, and as for the rest, we don't expect to ever know what kind of entity is targeting our sites or why. - In the fall Bulletin, we wrote about the August attack on gnu.org. That attack continues, but we have mitigated it. Judging from the pattern and scope, the goal was likely to take the site down and it was not an LLM crawler. We do not know who or what is behind the attack, but since then, we have had more attacks with even higher severity. - To begin with, GNU Savannah, the FSF's collaborative software development system, was hit by a massive botnet controlling about five million IPs starting in January. As of this writing, the attack is still ongoing, but the botnet's current iteration is mitigated. The goal is likely to build an LLM training dataset. We do not know who or what is behind this. - Furthermore, gnu.org and ftp.gnu.org were targets in a new DDoS attack starting on May 27, 2025. Its goal seems to be to take the site down. It is currently mitigated. It has had several iterations, and each has caused some hours of downtime while we figured out how to defend ourselves against it. Here again, the goal was likely to take our sites down and we do not know who or what is behind this. - In addition, directory.fsf.org, the server behind the Free Software Directory, has been under attack since June 18. This likely is an LLM scraper designed to specifically target Media Wiki sites with a botnet. This attack is very active and now partially mitigated... Even though we are under active attack, gnu.org, ftp.gnu.org, and savannah.gnu.org are up with normal response times at the moment, and have been for the majority of this week, largely thanks to hard work from the Savannah hackers Bob, Corwin, and Luke who've helped us, your sysadmins. We've shielded these sites for almost a full year of intense attacks now, and we'll keep on fighting these attacks for as long as they continue. The full-time FSF tech staff is just two systems administrators, "and we currently lack the funds to hire more tech staff any time soon," Kelling points out. Kelling titled his post "our small team vs millions of bots," suggesting that supporters purchase FSF memberships "to improve our staffing situation... Can you join us in our crucial work to guard user freedom and defy dystopia?" Kelling also points out they're also facing "run-of-the-mill standard crawlers, SEO crawlers, crawlers pretending to be normal users, crawlers pretending to be other crawlers, uptime systems, vulnerability scanners, carrier-grade network address translation, VPNs, and normal browsers hitting our sites..." "Some of the abuse is not unique to us, and it seems that the health of the web has some serious problems right now."
 
Read more of this story at Slashdot.
- Interstellar Navigation Demonstrated for the First Time With NASA's 'New Horizons'
Three space probes are leaving our solar system — yet are still functioning. After the two Voyager space probes, New Horizons "was launched in 2006, initially to study Pluto," remembers New Scientist. But "it has since travelled way beyond this point, ploughing on through the Kuiper belt, a vast, wide band of rocks and dust billions of miles from the sun. It is now speeding at tens of thousands of kilometres per hour..." And it's just performed the first ever example of interstellar navigation...As it hurtles out of our solar system, NASA's New Horizons spacecraft is so far from Earth that the stars in the Milky Way appear in markedly different positions compared with our own view... due to the parallax effect. This was demonstrated in 2020 when the probe beamed back pictures of two nearby stars, Proxima Centauri and Wolf 359, to Earth. Now, Tod Lauer at the US National Optical-Infrared Astronomy Research Laboratory in Arizona and his colleagues have used this effect to work out the position of New Horizons... Almost all spacecraft calculate their bearings to within tens of metres using NASA's Deep Space Network, a collection of radio transmitters on Earth that send regular signals out to space. In comparison, the parallax method was far less accurate, locating New Horizons within a sphere with a radius of 60 million kilometres, about half the distance between Earth and the sun. "We're not going to put the Deep Space Network out of business — this is only a demo proof of concept," says Lauer. However, with a better camera and equipment they could improve the accuracy by up to 100 times, he says. Using this technique for interstellar navigation could offer advantages over the DSN because it could give more accurate location readings as a spacecraft gets further away from Earth, as well as being able to operate autonomously without needing to wait for a radio signal to come from our solar system, says Massimiliano Vasile at the University of Strathclyde, UK. "If you travel to an actual star, we are talking about light years," says Vasile. "What happens is that your signal from the Deep Space Network has to travel all the way there and then all the way back, and it's travelling at the speed of light, so it takes years." Just like a ship's captain sailing by the stars, "We have a good enough three-dimensional map of the galaxy around us that you can find out where you are," Lauer says. So even when limiting your navigation to what's on-board the spacecraft, "It's a remarkable accuracy, with your own camera!"
 
Read more of this story at Slashdot.
- Police Department Apologizes for Sharing AI-Doctored Evidence Photo on Social Media
A Maine police department has now acknowledged "it inadvertently shared an AI-altered photo of drug evidence on social media," reports Boston.com:The image from the Westbrook Police Department showed a collection of drug paraphernalia purportedly seized during a recent drug bust on Brackett Street, including a scale and white powder in plastic bags. According to Westbrook police, an officer involved in the arrests snapped the evidence photo and used a photo editing app to insert the department's patch. "The patch was added, and the photograph with the patch was sent to one of our Facebook administrators, who posted it," the department explained in a post. "Unbeknownst to anyone, when the app added the patch, it altered the packaging and some of the other attributes on the photograph. None of us caught it or realized it." It wasn't long before the edited image's gibberish text and hazy edges drew criticism from social media users. According to the Portland Press Herald, Westbrook police initially denied AI had been used to generate the photo before eventually confirming its use of the AI chatbot ChatGPT. The department issued a public apology Tuesday, sharing a side-by-side comparison of the original and edited images. "It was never our intent to alter the image of the evidence," the department's post read. "We never realized that using a photoshop app to add our logo would alter a photograph so substantially."
 
Read more of this story at Slashdot.

- Yes, I wrote a very expensive bug. In my defense I was only seven years old at the time
Years later, deep into a great tech career, your fellow reader remains inspired by the forgiveness received after the error
Who, Me? Monday morning brings many readers a return to the world of adults, which The Register marks by bringing you a new edition of Who, Me? It's the reader-contributed column in which you share stories of making mistakes for which you are somehow forgiven.…
- Atlassian migrated 4 million Postgres databases to shrink AWS bill
PLUS: Lexmark’s Chinese owners sell to Xerox; India, Australia, target underwater drones; JPMorgan drops custom TLDs; and more!
Asia In Brief Australian collaborationware company Atlassian has migrated the four million Postgres databases that back its customers’ Jira implementations to Amazon Web Services’ Aurora.…
- Stalkerware firm gets scooped by SQL-slinging security snoop
Also, Swiss ransomware posture looks like its cheese, the CVE Program wants YOU, more sus checks and more
Infosec In Brief A security researcher looking at samples of stalkerware discovered an SQL vulnerability that allowed him to steal a database of 62,000 user accounts. …
- Ingram Micro confirms ransomware behind multi-day outage
SafePay crew claims responsibility for intrusion at one of world's largest tech distributors
Ingram Micro, one of the world's largest distributors, has confirmed it is trying to restore systems following a ransomware attack.…
- Massive spike in use of .es domains for phishing abuse
¡Cuidado! Time to double-check before entering your Microsoft creds
Cybersecurity experts are reporting a 19x increase in malicious campaigns being launched from .es domains, making it the third most common, behind only .com and .ru.…

- Using OpenTelemetry and the OTel Collector for Logs, Metrics, and Traces
OpenTelemetry (fondly known as OTel) is an open-source project that provides a unified set of APIs, libraries, agents, and instrumentation to capture and export logs, metrics, and traces from applications. The project’s goal is to standardize observability across various services and applications, enabling better monitoring and troubleshooting. Read More at Causely
The post Using OpenTelemetry and the OTel Collector for Logs, Metrics, and Traces appeared first on Linux.com.
- Xen 4.19 is released
Xen Project 4.19 has been officially out since July 31st, 2024, and it brings significant updates. With enhancements in performance, security, and versatility across various architectures like Arm, PPC, RISC-V, and x86, this release is an important milestone for the Xen community. Read more at XCP-ng Blog
The post Xen 4.19 is released appeared first on Linux.com.
- Advancing Xen on RISC-V: key updates
At Vates, we are heavily invested in the advancement of Xen and the RISC-V architecture. RISC-V, a rapidly emerging open-source hardware architecture, is gaining traction due to its flexibility, scalability and openness, which align perfectly with our ethos of fostering open development ecosystems. Although the upstream version of Xen for RISC-V is not yet fully [0]
The post Advancing Xen on RISC-V: key updates appeared first on Linux.com.
- AI Produces Data-driven OpenFOAM Speedup (HPC Wire)
Researchers from TU Darmstadt, TU Dresden, Hewlett Packard Enterprise (HPE), and Intel have developed advanced applications that combine HPC simulations with AI techniques using the open-source computational fluid dynamics solver OpenFOAM and the HPE-led SmartSim AI/ML library. These applications show promise for improving the accuracy and capabilities of traditional scientific and engineering modelling with data-driven [0]
The post AI Produces Data-driven OpenFOAM Speedup (HPC Wire) appeared first on Linux.com.

- Linux 6.16 Performance Regression Tracked Down In New Futex Code
Sent out this morning as part of this week's "locking/urgent" pull request is a performance regression fix ahead of today's Linux 6.16-rc5 release. This latest performance regression in the Linux kernel is around the new Futex code merged this cycle with a big performance hit being observed in scheduler benchmarks...

- WinUAE 6.0.0 released
WinUAE has released version 6.0.0 of the Windows version of the UAE Amiga emulator, packing a truly terrifying number of changes, improvements, and fixes. Major update to custom chipset emulation. Internally almost everything in main chipset emulation has been rewritten. Fastest possible/JIT mode chipset timing/sync had major changes which can cause side-effects. Bugs are very possible, especially in very rarely used features. ↫ WinUAE website Going through the changelog is dizzying, ranging from an almost complete rewrite of the main chipset emulation for internal cycle accuracy, to running the emulation of the Denise/Lisa chips in a separate thread for better performance, to a ton of fixes and smaller updates.
- MacOS� icons keep getting worse every time Apple touches them
With macOS 26, Apple has announced a dramatically new look to their UI: Liquid Glass. Solid material icon elements give way to softer, shinier, glassier icons. The rounded rectangle became slightly more rounded, and Apple eliminated the ability for icon elements to extend beyond the icon rectangle (as seen in the current icons for GarageBand, Photo Booth, Dictionary, etc.). With this release being one of the most dramatic visual overhauls of macOS�s design, I wanted to begin a collection chronicling the evolution of the system icons over the years. I�ve been rolling these out on social media over the past week and will continue to add to and update this collection slowly over the summer. Enjoy! ↫ BasicAppleGuy Every single one of these icons is getting progressively worse with almost every design change. They go from beautifully crafted, easily readable and supremely distinguishable icons to generic, repetitive blobs of colour, void of any personality, artistry, or usability considerations. Also, Apple�s new icon design language makes the icons look fuzzy, like they�re not being rendered properly. It�s very unnerving. The one exception is probably the generic folder icon, which looks fine in all of its incarnations. Then there�s the classic Platinum, pixelated version from Mac OS 9 and earlier, which, together with icons from Windows and BeOS from the same time period, are a whole different style that I don�t think most people would accept anymore these days, but that I absolutely adore. Mostly I�m just sad that the craft of making exquisite icons for operating systems is dying, replaced by what almost look like AI! generated blobs of indeterminate meaning, that rely more on preexisting knowledge of the operating system and its applications in question than on being recognisable and decipherable by anyone. I truly hope Windows and the various open source desktops don�t follow in Apple�s footsteps here.
- Tone-deaf Xbox executive urges laid off employees to talk to Copilot for emotional support
A couple of days ago, Microsoft announced 9,000 layoffs across its global workforce, impacting its engineering, Xbox, sales, and management teams. This move also affected various initiatives, resulting in the cancellation of at least three Xbox games, job cuts across various studios, and even the shuttering of one game studio, The Initiative. In the wake of this dark day in the the tech industry, a tone-deaf Microsoft executive urged laid off workers to turn to AI tools for emotional support. ↫ Usama Jawad at Neowin These corporations are raking in massive amounts of profit, they�re doing better than ever, the cup of money runneth over, and yet, they keep laying off thousands and thousands of people almost every few months. The incentives in modern-day capitalism clearly aren�t working out for the vast majority of people, and then to give that final kick when you�re already down, some asshat manager tells you to talk to! sparkly autocomplete for emotional support. Fuck this guy.
- NVIDIA is full of shit
Since the disastrous launch of the RTX 50 series, NVIDIA has been unable to escape negative headlines: scalper bots are snatching GPUs away from consumers before official sales even begin, power connectors continue to melt, with no fix in sight, marketing is becoming increasingly deceptive, GPUs are missing processing units when they leave the factory, and the drivers, for which NVIDIA has always been praised, are currently falling apart. And to top it all off, NVIDIA is becoming increasingly insistent that media push a certain narrative when reporting on their hardware. ↫ Sebin Nyshkim Out of all the issues listed here � and there are many, and each is bad enough on their own � it�s the frame generation and related pressure campaigns on reviewers that really get on my nerves the most. Technologies like DLSS (rendering at a lower internal resolution scaling that up) and frame generation (injecting fake AI! frames to jack up the frame rate) can be fine technologies when used at the consumer�s discretion to find a balance between improved perceived performance in exchange for blurry image quality and artefacting, but we�ve now reached a point where NVIDIA will only boast about performance figures with these technologies enabled, downsides be damned. If that wasn�t misleading enough, the company is also pressuring reviewers who don�t enable these technologies, and focus on real frames, real resolutions, and this, real performance. If you don�t comply, you�re not getting the next crop of GPUs in early access. It�s the kind of shit Apple pulls all the time, and we need less of it, not more. Just don�t buy NVIDIA. They�re already a terrible choice if you�re running anything other than Windows, but the company�s recent behaviour and serious missteps have made the choice for AMD or Intel only more obvious.
- Redox gets network booting, work on UNIX domain sockets continues
Redox continues to make progress, and as another month has passed us by, it�s time for another monthly update. This past month, the focus has been on UNIX domain sockets, which are needed for Redox� goal of running Wayland. As we continue to move forward with our plans for Wayland, a key technology for Wayland support is the ability to send file descriptors over Unix Domain Sockets. File descriptor sending is also an important part of many other OS features, including Capability-based Security. Our Redox Summer of Code project to implement that ability has been progressing very well. Ibuki, a new member of the Redox team, has jumped right into the deep end, and implemented the sendmg and recvmsg functionality, and continues to move forward with work on UDS. ↫ Ribbon and Ron Williams You can read more about the UNIX domain sockets progress in a detailed post on the Redox website. Redox now also supports network booting through PXE, but for now, only UEFI is supported. Of course, all of this work is topped off with the usual slew of fixes in relibc, RedoxFS, various drivers, and more, as well updated ports across the board.
- Is an Intel N100 a better value than a Raspberry Pi?
All of this to say: value is complicated. The Pi 5 is`much`more compact and slightly more power efficient (especially at idle) compared to the cheapest N1XX Intel systems. The Intel systems are better suited for a desktop use case. The Pi 5 can be run off PoE power, for easier one-cable networking + power. The Intel systems are more compatible with a wider range of software (not the least of which is`anything requiring Windows). ↫ Jeff Geerling Intel�s N100 and N150 are vastly underappreciated. The mini laptop I reviewed over a year ago is built around the N100, and I still use it every day for watching YouTube, writing OSNews posts, and so on. I never run into performance issues, battery life is excellent, and I don�t have to deal with the annoyances of using ARM. The catch is that you�re going to want to use Linux � I use Fedora KDE � because Windows� performance on the N100 is dreadful. I don�t think the jump from the N100 to the N150 is worthwhile enough to buy the new version of my mini laptop, so I�ll stick with what I have. I do hope Intel continues the Nxxx line or processors, because it offers something no other x86 chip offers: more than reasonable performance at low power usage for an incredibly low price.
- Ubuntu 25.10 to drop support for effectively all existing RISC-V hardware, focuses on future RISC-V hardware instead
A recent bug report filed against Ubuntu’s upgrading tool confirmed a major change with regards to the RISC-V requirements for the upcoming Ubuntu 25.10 release — most existing RISC-V devices will`not`be able to run Ubuntu 25.10. How come? ↫ Joey Sneddon at omgubuntu.co.uk RISC-V just isn�t delivering. That�s the cold and harsh truth more and more people are having to deal with, such as Chimera Linux dropping RISC-V support because the ecosystem is simply lacking the kind of powerful and available hardware to sustain itself (Chimera got lucky, though, and gained access to a Milk-V Pioneer through Adélie Linux). The number of systems and boards that are both powerful and available is close enough to zero that it might as well be zero, and if neither users nor developers can buy RISC-V hardware, what�s the point in supporting it? The issue for Ubuntu specifically is that version 25.10 of the distribution intends to target only the RVA23 baseline RISC-V profile, while currently Ubuntu supports RVA20 as the baseline. This higher baseline profile requires a number of extensions to the instruction set that no existing hardware yet supports, making 25.10 effectively a clean break for all existing RISC-V hardware. In other words, if you�re running Ubuntu on RISC-V hardware today, you won�t be able to upgrade to 25.10 or higher. RISC-V really needs vastly improved hardware availability, because right now it�s just not delivering on the years of promises.
- The Amiga 3000 UNIX and Sun Microsystems: deal or no deal?
Amiga lore is full of exciting tales. Many of them are retold to demonstrate how the incompetence of Commodore�s management destroyed a platform that, by rights, was destined for success.`Coulda, shoulda,`and the Amiga`woulda`risen as rightful ruler of all other computer platforms, forever and ever. Amen. One of those stories is about how Sun Microsystems allegedly showed interest in the Amiga 3000 during the early 1990s. It�s a classic Amiga anecdote, usually recounted without much reflection, and one`I�ve certainly helped perpetuate. Alas, the more I think about it, the less it adds up. Fact or factoid? Let�s speculate! ↫ Carl Svensson Great speculation with some solid reasoning and sourcing. Considering that had been some minor joint marketing between Sun and Commodore, my money is on the talks around that deal birthing rumours about more extensive Sun involvement in the Amiga 3000. At this point in time, however, decades after the fact and with several conflicting account, it�s unlikely we�ll ever get a solid answer.
- AI note takers are flooding Zoom calls as workers opt to skip meetings
Clifton Sellers attended a Zoom meeting last month where robots outnumbered humans. He counted six people on the call including himself, Sellers recounted in an interview. The 10 others attending were note-taking apps powered by artificial intelligence that had joined to record, transcribe and summarize the meeting. ↫ Lisa Bonos and Danielle Abril at The Bezos Post Management strongly encourages � mandates � that everyone use AI! to improve productivity, but then gets all uppity when people actually do. Welcome to finding out!.
- Elementary OS makes meaningful accessibility improvements
With recent efforts to improve accessibility in GNOME and KDE, as well as a renewed focus on highlighting the many issues that still need fixing, the Linux desktop is making meaningful strides in becoming more accessible to those among us with disabilities. Obviously, the Linux desktop is bigger than just GNOME and KDE, so today we have elementary OS improving its accessibility features in a variety of ways. July is Disability Pride Month, an opportunity for us to consider how we’re serving our disabled community and work on breaking down barriers to access. Last year we had the pleasure of being introduced to Florian—a fully blind cybersecurity enthusiast—and thanks to his feedback we completely rewrote navigation in Onboarding to be more keyboard and screen reader friendly, as well as took another look at Installation and Initial Setup to vastly improve our entire first run experience for blind folks. Plus, we implemented the screen reader interface in the + window switcher. Thanks to this feedback, elementary OS 8 can be installed and set up completely blind, an important win for maintaining your independence as a person with vision disabilities. Since the release of OS 8 we’ve been working on things like improving contrast, support for Dark Mode screenshots and brand colors in AppCenter, turning on or snoozing Dark Mode without canceling your schedule, expanding the scope of the “Reduce Motion” setting, and adding more options to reduce distracting notification bubbles. Plus, thanks to feedback from Aaron who you may know from his blog series on Linux accessibility, Notifications and the Shortcut Overlay both got releases that add screen reader support. ↫ Danielle Foré at elementary�s blog I�m glad we�re finally putting to rest this idea that accessibility features should be afterthoughts, relevant to only a minute percentage of people. Not only is the disabled community way bigger than we might think, many of the features they require are simply also extremely nice and beneficial to users who might not actually require them. I know tons of people who, for instance, love reduce motion features simply because it makes their operating system feel faster, or people who just don�t want to be bothered with notifications the instant they arrive. Accessibility goes far beyond what we traditionally think of as accessibility features, like screen readers or high contrast modes. Making software more accessible for those that require it, also makes software more accessible for those that merely desire it. Even though elementary OS probably isn�t the type of distribution that appeals to the average OSNews reader, I�m incredibly happy they�re taking accessibility seriously, and I intend to continue to highlight such improvements.

- EU OS: A Bold Step Toward Digital Sovereignty for Europe
Image 
A new initiative, called "EU OS," has been launched to develop a Linux-based operating system tailored specifically for the public sector organizations of the European Union (EU). This community-driven project aims to address the EU's unique needs and challenges, focusing on fostering digital sovereignty, reducing dependency on external vendors, and building a secure, self-sufficient digital ecosystem.
What Is EU OS?
EU OS is not an entirely novel operating system. Instead, it builds upon a Linux foundation derived from Fedora, with the KDE Plasma desktop environment. It draws inspiration from previous efforts such as France's GendBuntu and Munich's LiMux, which aimed to provide Linux-based systems for public sector use. The goal remains the same: to create a standardized Linux distribution that can be adapted to different regional, national, and sector-specific needs within the EU.
Rather than reinventing the wheel, EU OS focuses on standardization, offering a solid Linux foundation that can be customized according to the unique requirements of various organizations. This approach makes EU OS a practical choice for the public sector, ensuring broad compatibility and ease of implementation across diverse environments.
The Vision Behind EU OS
The guiding principle of EU OS is the concept of "public money – public code," ensuring that taxpayer money is used transparently and effectively. By adopting an open-source model, EU OS eliminates licensing fees, which not only lowers costs but also reduces the dependency on a select group of software vendors. This provides the EU’s public sector organizations with greater flexibility and control over their IT infrastructure, free from the constraints of vendor lock-in.
Additionally, EU OS offers flexibility in terms of software migration and hardware upgrades. Organizations can adapt to new technologies and manage their IT evolution at a manageable cost, both in terms of finances and time.
However, there are some concerns about the choice of Fedora as the base for EU OS. While Fedora is a solid and reliable distribution, it is backed by the United States-based Red Hat. Some argue that using European-backed projects such as openSUSE or KDE's upcoming distribution might have aligned better with the EU's goal of strengthening digital sovereignty.
Conclusion
EU OS marks a significant step towards Europe's digital independence by providing a robust, standardized Linux distribution for the public sector. By reducing reliance on proprietary software and vendors, it paves the way for a more flexible, cost-effective, and secure digital ecosystem. While the choice of Fedora as the base for the project has raised some questions, the overall vision of EU OS offers a promising future for Europe's public sector in the digital age.
Source: It's FOSS
European Union
- Linus Torvalds Acknowledges Missed Release of Linux 6.14 Due to Oversight
Linus Torvalds Acknowledges Missed Release of Linux 6.14 Due to Oversight
Linux kernel lead developer Linus Torvalds has admitted to forgetting to release version 6.14, attributing the oversight to his own lapse in memory. Torvalds is known for releasing new Linux kernel candidates and final versions on Sunday afternoons, typically accompanied by a post detailing the release. If he is unavailable due to travel or other commitments, he usually informs the community ahead of time, so users don’t worry if there’s a delay.
In his post on March 16, Torvalds gave no indication that the release might be delayed, instead stating, “I expect to release the final 6.14 next weekend unless something very surprising happens.” However, Sunday, March 23rd passed without any announcement.
On March 24th, Torvalds wrote in a follow-up message, “I’d love to have some good excuse for why I didn’t do the 6.14 release yesterday on my regular Sunday afternoon schedule,” adding, “But no. It’s just pure incompetence.” He further explained that while he had been clearing up unrelated tasks, he simply forgot to finalize the release. “D'oh,” he joked.
Despite this minor delay, Torvalds’ track record of successfully managing the Linux kernel’s development process over the years remains strong. A single day’s delay is not critical, especially since most Linux users don't urgently need the very latest version.
The new 6.14 release introduces several important features, including enhanced support for writing drivers in Rust—an ongoing topic of discussion among developers—support for Qualcomm’s Snapdragon 8 Elite mobile chip, a fix for the GhostWrite vulnerability in certain RISC-V processors from Alibaba’s T-Head Semiconductor, and a completed NTSYNC driver update that improves the WINE emulator’s ability to run Windows applications, particularly games, on Linux.
Although the 6.14 release went smoothly aside from the delay, Torvalds expressed that version 6.15 may present more challenges due to the volume of pending pull requests. “Judging by my pending pile of pull requests, 6.15 will be much busier,” he noted.
You can download the latest kernel here.
Linus Torvalds kernel
- AerynOS 2025.03 Alpha Released with GNOME 48, Mesa 25, and Linux Kernel 6.13.8
Image 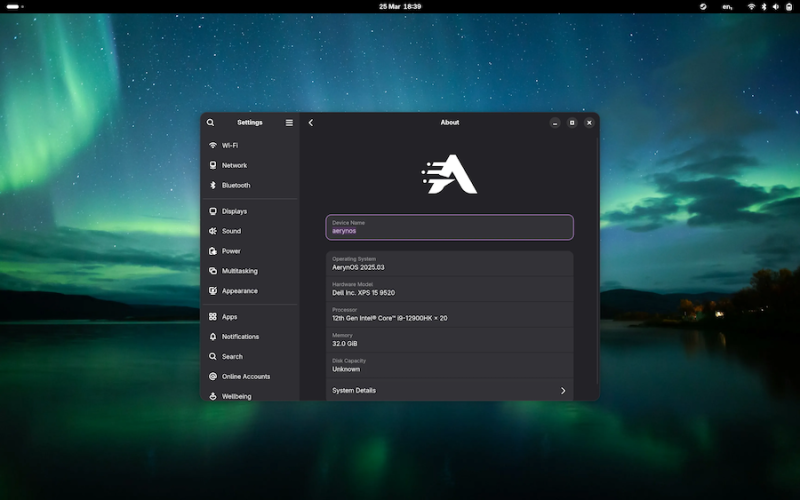
AerynOS 2025.03 has officially been released, introducing a variety of exciting features for Linux users. The release includes the highly anticipated GNOME 48 desktop environment, which comes with significant improvements like HDR support, dynamic triple buffering, and a Wayland color management protocol. Other updates include a battery charge limiting feature and a Wellbeing option aimed at improving user experience.
This release, while still in alpha, incorporates Linux kernel 6.13.8 and the updated Mesa 25.0.2 graphics stack, alongside tools like LLVM 19.1.7 and Vulkan SDK 1.4.309.0. Additionally, the Moss package manager now integrates os-info to generate more detailed OS metadata via a JSON file.
Future plans for AerynOS include automated package updates, easier rollback management, improved disk handling with Rust, and fractional scaling enabled by default. The installer has also been revamped to support full disk wipes and dynamic partitioning.
Although still considered an alpha release, AerynOS 2025.03 can be downloaded and tested right now from its official website.
Source: 9to5Linux
AerynOS
- Xojo 2025r1: Big Updates for Developers with Linux ARM Support, Web Drag and Drop, and Direct App Store Publishing
Image 
Xojo has just rolled out its latest release, Xojo 2025 Release 1, and it’s packed with features that developers have been eagerly waiting for. This major update introduces support for running Xojo on Linux ARM, including Raspberry Pi, brings drag-and-drop functionality to the Web framework, and simplifies app deployment with the ability to directly submit apps to the macOS and iOS App Stores.
Here’s a quick overview of what’s new in Xojo 2025r1:
1. Linux ARM IDE Support
Xojo 2025r1 now allows developers to run the Xojo IDE on Linux ARM devices, including popular platforms like Raspberry Pi. This opens up a whole new world of possibilities for developers who want to create apps for ARM-based devices without the usual complexity. Whether you’re building for a Raspberry Pi or other ARM devices, this update makes it easier than ever to get started.
2. Web Drag and Drop
One of the standout features in this release is the addition of drag-and-drop support for web applications. Now, developers can easily drag and drop visual controls in their web projects, making it simpler to create interactive, user-friendly web applications. Plus, the WebListBox has been enhanced with support for editable cells, checkboxes, and row reordering via dragging. No JavaScript required!
3. Direct App Store Publishing
Xojo has also streamlined the process of publishing apps. With this update, developers can now directly submit macOS and iOS apps to App Store Connect right from the Xojo IDE. This eliminates the need for multiple steps and makes it much easier to get apps into the App Store, saving valuable time during the development process.
4. New Desktop and Mobile Features
This release isn’t just about web and Linux updates. Xojo 2025r1 brings some great improvements for desktop and mobile apps as well. On the desktop side, all projects now include a default window menu for macOS apps. On the mobile side, Xojo has introduced new features for Android and iOS, including support for ColorGroup and Dark Mode on Android, and a new MobileColorPicker for iOS to simplify color selection.
5. Performance and IDE Enhancements
Xojo’s IDE has also been improved in several key areas. There’s now an option to hide toolbar captions, and the toolbar has been made smaller on Windows. The IDE on Windows and Linux now features modern Bootstrap icons, and the Documentation window toolbar is more compact. In the code editor, developers can now quickly navigate to variable declarations with a simple Cmd/Ctrl + Double-click. Plus, performance for complex container layouts in the Layout Editor has been enhanced.
What Does This Mean for Developers?
Xojo 2025r1 brings significant improvements across all the platforms that Xojo supports, from desktop and mobile to web and Linux. The added Linux ARM support opens up new opportunities for Raspberry Pi and ARM-based device development, while the drag-and-drop functionality for web projects will make it easier to create modern, interactive web apps. The ability to publish directly to the App Store is a game-changer for macOS and iOS developers, reducing the friction of app distribution.
How to Get Started
Xojo is free for learning and development, as well as for building apps for Linux and Raspberry Pi. If you’re ready to dive into cross-platform development, paid licenses start at $99 for a single-platform desktop license, and $399 for cross-platform desktop, mobile, or web development. For professional developers who need additional resources and support, Xojo Pro and Pro Plus licenses start at $799. You can also find special pricing for educators and students.
Download Xojo 2025r1 today at xojo.com.
Final Thoughts
With each new release, Xojo continues to make cross-platform development more accessible and efficient. The 2025r1 release is no exception, delivering key updates that simplify the development process and open up new possibilities for developers working on a variety of platforms. Whether you’re a Raspberry Pi enthusiast or a mobile app developer, Xojo 2025r1 has something for you.
Xojo ARM
- New 'Mirrored' Network Mode Introduced in Windows Subsystem for Linux
Microsoft's Windows Subsystem for Linux (WSL) continues to evolve with the release of WSL 2 version 0.0.2. This update introduces a set of opt-in preview features designed to enhance performance and compatibility.
Key additions include "Automatic memory reclaim" which dynamically optimizes WSL's memory footprint, and "Sparse VHD" to shrink the size of the virtual hard disk file. These improvements aim to streamline resource usage.
Additionally, a new "mirrored networking mode" brings expanded networking capabilities like IPv6 and multicast support. Microsoft claims this will improve VPN and LAN connectivity from both the Windows host and Linux guest.
Complementing this is a new "DNS Tunneling" feature that changes how DNS queries are resolved to avoid compatibility issues with certain network setups. According to Microsoft, this should reduce problems connecting to the internet or local network resources within WSL.
Advanced firewall configuration options are also now available through Hyper-V integration. The new "autoProxy" feature ensures WSL seamlessly utilizes the Windows system proxy configuration.
Microsoft states these features are currently rolling out to Windows Insiders running Windows 11 22H2 Build 22621.2359 or later. They remain opt-in previews to allow testing before final integration into WSL.
By expanding WSL 2 with compelling new capabilities in areas like resource efficiency, networking, and security, Microsoft aims to make Linux on Windows more performant and compatible. This evolutionary approach based on user feedback highlights Microsoft's commitment to WSL as a key part of the Windows ecosystem.
Windows
- Linux Threat Report: Earth Lusca Deploys Novel SprySOCKS Backdoor in Attacks on Government Entities
The threat actor Earth Lusca, linked to Chinese state-sponsored hacking groups, has been observed utilizing a new Linux backdoor dubbed SprySOCKS to target government organizations globally.
As initially reported in January 2022 by Trend Micro, Earth Lusca has been active since at least 2021 conducting cyber espionage campaigns against public and private sector targets in Asia, Australia, Europe, and North America. Their tactics include spear-phishing and watering hole attacks to gain initial access. Some of Earth Lusca's activities overlap with another Chinese threat cluster known as RedHotel.
In new research, Trend Micro reveals Earth Lusca remains highly active, even expanding operations in the first half of 2023. Primary victims are government departments focused on foreign affairs, technology, and telecommunications. Attacks concentrate in Southeast Asia, Central Asia, and the Balkans regions.
After breaching internet-facing systems by exploiting flaws in Fortinet, GitLab, Microsoft Exchange, Telerik UI, and Zimbra software, Earth Lusca uses web shells and Cobalt Strike to move laterally. Their goal is exfiltrating documents and credentials, while also installing additional backdoors like ShadowPad and Winnti for long-term spying.
The Command and Control server delivering Cobalt Strike was also found hosting SprySOCKS - an advanced backdoor not previously publicly reported. With roots in the Windows malware Trochilus, SprySOCKS contains reconnaissance, remote shell, proxy, and file operation capabilities. It communicates over TCP mimicking patterns used by a Windows trojan called RedLeaves, itself built on Trochilus.
At least two SprySOCKS versions have been identified, indicating ongoing development. This novel Linux backdoor deployed by Earth Lusca highlights the increasing sophistication of Chinese state-sponsored threats. Robust patching, access controls, monitoring for unusual activities, and other proactive defenses remain essential to counter this advanced malware.
The Trend Micro researchers emphasize that organizations must minimize attack surfaces, regularly update systems, and ensure robust security hygiene to interrupt the tactics, techniques, and procedures of relentless threat groups like Earth Lusca.
Security
- Linux Kernel Faces Reduction in Long-Term Support Due to Maintenance Challenges
The Linux kernel is undergoing major changes that will shape its future development and adoption, according to Jonathan Corbet, Linux kernel developer and executive editor of Linux Weekly News. Speaking at the Open Source Summit Europe, Corbet provided an update on the latest Linux kernel developments and a glimpse of what's to come.
A major change on the horizon is a reduction in long-term support (LTS) for kernel versions from six years to just two years. Corbet explained that maintaining old kernel branches indefinitely is unsustainable and most users have migrated to newer versions, so there's little point in continuing six years of support. While some may grumble about shortened support lifecycles, the reality is that constantly backporting fixes to ancient kernels strains maintainers.
This maintainer burnout poses a serious threat, as Corbet highlighted. Maintaining Linux is largely a volunteer effort, with only about 200 of the 2,000+ developers paid for their contributions. The endless demands on maintainers' time from fuzz testing, fixing minor bugs, and reviewing contributions takes a toll. Prominent maintainers have warned they need help to avoid collapse. Companies relying on Linux must realize giving back financially is in their interest to sustain this vital ecosystem.
The Linux kernel is also wading into waters new with the introduction of Rust code. While Rust solves many problems, it also introduces new complexities around language integration, evolving standards, and maintainer expertise. Corbet believes Rust will pass the point of no return when core features depend on it, which may occur soon with additions like Apple M1 GPU drivers. Despite skepticism in some corners, Rust's benefits likely outweigh any transition costs.
On the distro front, Red Hat's decision to restrict RHEL cloning sparked community backlash. While business considerations were at play, Corbet noted technical factors too. Using older kernels with backported fixes, as RHEL does, risks creating divergent, vendor-specific branches. The Android model of tracking mainline kernel dev more closely has shown security benefits. Ultimately, Linux works best when aligned with the broader community.
In closing, Corbet recalled the saying "Linux is free like a puppy is free." Using open source seems easy at first, but sustaining it long-term requires significant care and feeding. As Linux is incorporated into more critical systems, that maintenance becomes ever more crucial. The kernel changes ahead are aimed at keeping Linux healthy and vibrant for the next generation of users, businesses, and developers.
kernel
- Linux Celebrates 32 Years with the Release of 6.6-rc2 Version
Today marks the 32nd anniversary of Linus Torvalds introducing the inaugural Linux 0.01 kernel version, and celebrating this milestone, Torvalds has launched the Linux 6.6-rc2. Among the noteworthy updates are the inclusion of a feature catering to the ASUS ROG Flow X16 tablet's mode handling and the renaming of the new GenPD subsystem to pmdomain.
The Linux 6.6 edition is progressing well, brimming with exciting new features that promise to enhance user experience. Early benchmarks are indicating promising results, especially on high-core-count servers, pointing to a potentially robust and efficient update in the Linux series.
Here is what Linus Torvalds had to say in today's announcement:
Another week, another -rc.I think the most notable thing about 6.6-rc2 is simply that it'sexactly 32 years to the day since the 0.01 release. And that's a roundnumber if you are a computer person.Because other than the random date, I don't see anything that reallystands out here. We've got random fixes all over, and none of it looksparticularly strange. The genpd -> pmdomain rename shows up in thediffstat, but there's no actual code changes involved (make sure touse "git diff -M" to see them as zero-line renames).And other than that, things look very normal. Sure, the architecturefixes happen to be mostly parisc this week, which isn't exactly theusual pattern, but it's also not exactly a huge amount of changes.Most of the (small) changes here are in drivers, with some tracingfixes and just random things. The shortlog below is short enough toscroll through and get a taste of what's been going on. Linus Torvalds
- Introducing Bavarder: A User-Friendly Linux Desktop App for Quick ChatGPT Interaction
Want to interact with ChatGPT from your Linux desktop without using a web browser?
Bavarder, a new app, allows you to do just that.
Developed with Python and GTK4/libadwaita, Bavarder offers a simple concept: pose a question to ChatGPT, receive a response, and promptly copy the answer (or your inquiry) to the clipboard for pasting elsewhere.
With an incredibly user-friendly interface, you won't require AI expertise (or a novice blogger) to comprehend it. Type your question in the top box, click the blue send button, and wait for a generated response to appear at the bottom. You can edit or modify your message and repeat the process as needed.
During our evaluation, Bavarder employed BAI Chat, a GPT-3.5/ChatGPT API-based chatbot that's free and doesn't require signups or API keys. Future app versions will incorporate support for alternative backends, such as ChatGPT 4 and Hugging Chat, and allow users to input an API key to utilize ChatGPT3.
At present, there's no option to regenerate a response (though you can resend the same question for a potentially different answer). Due to the lack of a "conversation" view, tracking a dialogue or following up on answers can be challenging — but Bavarder excels for rapid-fire questions.
As with any AI, standard disclaimers apply. Responses might seem plausible but could contain inaccurate or false information. Additionally, it's relatively easy to lead these models into irrational loops, like convincing them that 2 + 2 equals 106 — so stay alert!
Overall, Bavarder is an attractive app with a well-defined purpose. If you enjoy ChatGPT and similar technologies, it's worth exploring.
ChatGPT AI
- LibreOffice 7.5.3 Released: Third Maintenance Update Brings 119 Bug Fixes to Popular Open-Source Office Suite
Today, The Document Foundation unveiled the release and widespread availability of LibreOffice 7.5.3, which serves as the third maintenance update to the current LibreOffice 7.5 open-source and complimentary office suite series.
Approximately five weeks after the launch of LibreOffice 7.5.2, LibreOffice 7.5.3 arrives with a new set of bug fixes for those who have successfully updated their GNU/Linux system to the LibreOffice 7.5 series.
LibreOffice 7.5.3 addresses a total of 119 bugs identified by users or uncovered by LibreOffice developers. For a more comprehensive understanding of these bug fixes, consult the RC1 and RC2 changelogs.
You can download LibreOffice 7.5.3 directly from the LibreOffice website��or from SourceForge as binary installers for DEB or RPM-based GNU/Linux distributions. A source tarball is also accessible for individuals who prefer to compile the software from sources or for system integrators.
All users operating the LibreOffice 7.5 office suite series should promptly update their installations to the new point release, which will soon appear in the stable software repositories of your GNU/Linux distributions.
In early February 2023, LibreOffice 7.5 debuted as a substantial upgrade to the widely-used open-source office suite, introducing numerous features and improvements. These enhancements encompass major upgrades to dark mode support, new application and MIME-type icons, a refined Single Toolbar UI, enhanced PDF Export, and more.
Seven maintenance updates will support LibreOffice 7.5 until November 30th, 2023. The next point release, LibreOffice 7.5.4, is scheduled for early June and will include additional bug fixes.
The Document Foundation once again emphasizes that the LibreOffice office suite's "Community" edition is maintained by volunteers and members of the Open Source community. For enterprise implementations, they suggest using the LibreOffice Enterprise family of applications from ecosystem partners.
LibreOffice

- Fedora Continues 32-Bit Support
In a move that should come as a relief to some portions of the Linux community, Fedora will continue supporting 32-bit architecture.
- ONLYOFFICE v9 Embraces AI
Like nearly all office suites on the market (except LibreOffice), ONLYOFFICE has decided to go the AI route.
|